How to Prepare for an Audit with your Client
Where to store your Documents and other Audit Information
Anti-Virus / Malware Protection
Collection-Master Claim Information
Goal
This document will help you better understand how you can leverage technology to make preparing for an audit with your client easier!
Where to store your Documents and other Audit Information
There are many places where you can store your information. It can be as simple as setting up folders on your network, using an application-specific to audits, or using some other repository.
At Vertican, we use Confluence by Atlassian This product is a Wiki that that provides a secure place to store documents, while assigning different levels of security to each staff member. It also maintains historical versioning with the ability to create comprehensive documents and then export them as PDFs or Word documents.
We use Confluence for all of our documentation needs. As an example, this document was created and maintained in a “Confluence Space.”
There are many other similar services including:
|
|
|
Information about your Firm
The client will ask you to provide information about your firm, e.g., contacts for the audit, administration, accounting, IT, collections, operations. Your client will request copies of your policies and procedures and ask detailed audit questions, such as IT specifics, as well as information on licenses, insurance, etc.
In an ideal world, every client would ask for the information in the same format, or even keep their audit the same each year, but change seems to be the only constant.
Your tool should be able to easily pick various documents and export them to PDFs.
IT Information
You will be asked several security questions about how you keep your clients’ data safe! Remember, security is a collection of layers with each protecting you from breaches. The most common breach will be due to something your own staff does, typically violating an internal policy. You should have strong security training for your in-house staff and provide tests regularly to ensure that they understand and live your security policy.
Your clients will ask for various monitors, scans, and tools to prevent information from leaking out, either intentionally or accidentally.
Be sure to minimize wireless connections to your network. Assume that someone can break into your wireless network despite any protection you might have in place. The same applies to cell phone connections.
Any connection to your system should be encrypted, e.g., wireless, cell, internet, and every wired connection. Ensuring that all your workstations are connected via SMB3 with encryption will ensure encryption in motion. This means that all of your workstations and servers must be modern Windows 10 / Windows 2016 Server or higher.
SQL Server and any other data repositories should be configured to require encryption.
Collection-Master should be configured as Client-Server and Secure Data. Using Secure Data will ensure that the actual data is safe. Client-Server uses an encrypted connection between the Client, the Listener, and the Server. All these encryption techniques are “encrypted in motion.”
Some drives support encryption at rest on a hardware level. If a firm uses a storage subsystem, the storage device becomes responsible for encrypting the data at rest. Avoid using software to encrypt data at rest.
Workstations
Some of your information will be stored at the physical workstation level. To protect this information, you should implement encryption at the workstation level. If you store information on a laptop and carry it out of the office the entire laptop should be encrypted.
Anti-Virus / Malware Protection
In the modern world, there are many bad actors trying to gain access to your system. In our industry, you are storing both PII and NPI, and this would be a major win for those bad actors if they gain access to this information. With the internet and remote access, there has been a shift from a time when storing your data on your own server was safest because no one could get to it.
Microsoft’s policy is to assume that someone is actively hacking and has access to their system. As security is a matter of layers, each layer protects you. They also retain more than 3,500 cyber professionals continually looking for security problems and addressing them as they are found. Remember that you might be protecting yourself from someone that you know and trust. How many full-time cyber professionals do you have monitoring your own system?
You can host your own equipment in a data center or move your solution to Microsoft Azure or Amazon Web Services (AWS). This is not a requirement, but it is a thought for your long-term security strategy.
Backups
You should always have a minimum of three backups and at least one of the backups should be off-site. Your ability to recover from a disaster (in a certain amount of time) will depend upon your relationship with your clients. You should also maintain historical backups. Every now and then someone needs to restore a file that is over a year old.
vMedia
vMedia has a very powerful exporter module that will allow you to export your documents in bulk. Occasionally, your client will pick 40 “random claims” and ask you to create an export of these selected documents for their review.
Use vMedia’s Viewing module to query and tag a list of documents and select the export option. Choose the Group & Compress Option if you want to build a single Zip file with all of the selected media. The Spectrum Exporter allows you to be more specific about the format that you want to use for exporting your media.
You can also use the Collection-Master vMedia tab to view individual documents. From there you can save the media to a folder.
Collection-Master Claim Information
Word Processing has an amazing amount of information. You can create an “Audit Document” that includes the information your client wants, and you can easily merge the documents on a list of claims. This audit information may be archived to vMedia so that there is a record.
In addition, many Collection-Master features use the “Select Screen.”
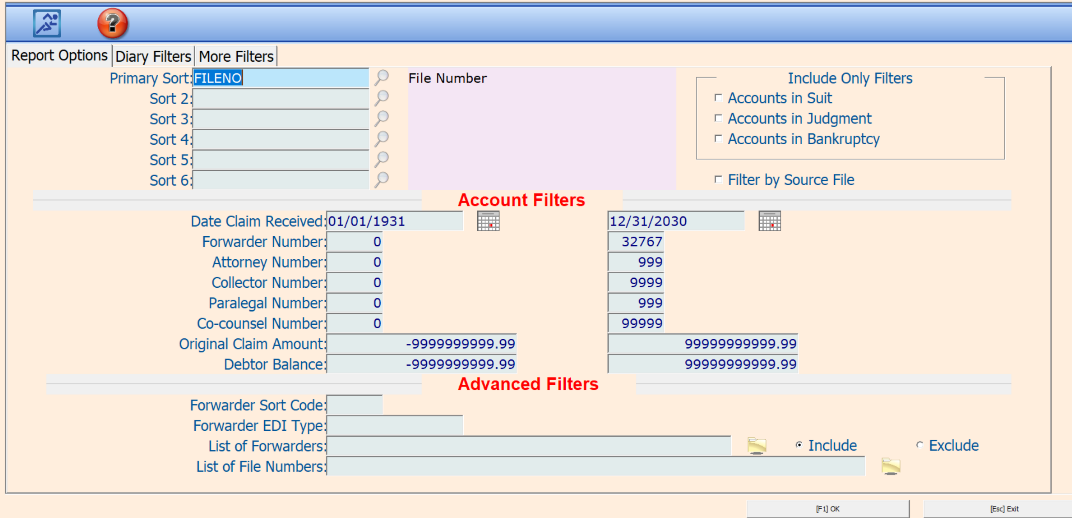
You can filter to look for special case examples or use my favorite: “List of File Numbers.” With this feature you will create a text file with the 40 or so claims that your client wants and then run the selected reports.
Paperless File [1-1-Shift F4]
Pull up your list of claims filtered by whatever you prefer and be presented a list of claims with summary information.
As you pull up the claims, you can perform any actions you want, such as:
- Review / Print Paperless DFile
- View Media & Export the information
- Screen Prints
- Instant Letters
- F11 – Claim Summary
When you are done working the claim, hit “Escape” and be returned to your list.
Even better, use Page Up/Page Down to browse through your claims.
Report Generator [3-2]
Using the “Select Screen,” pick a list of claims and generate a [3-2] report. This report can include claim summary information.
Paper Ledger Card [2-9]
The Paper Ledger Card [2-9] report has many different variations that show itemized accounting on a claim level. You may report on an individual claim or use the “Select Screen” to report on a group of claims. The HTML versions of the reports are “Excel friendly.”
Print Paperless Notes to File [4-1-5-7]
Use the “Select Screen” to select a list of claims and an individual HTM or web page will be created in your “N: folder.” The files will be named the same as the Forwarder File Number assigned to the claim. HTM documents may be loaded in Excel (Excel may complain about formatting, but it’s okay to ignore that.)
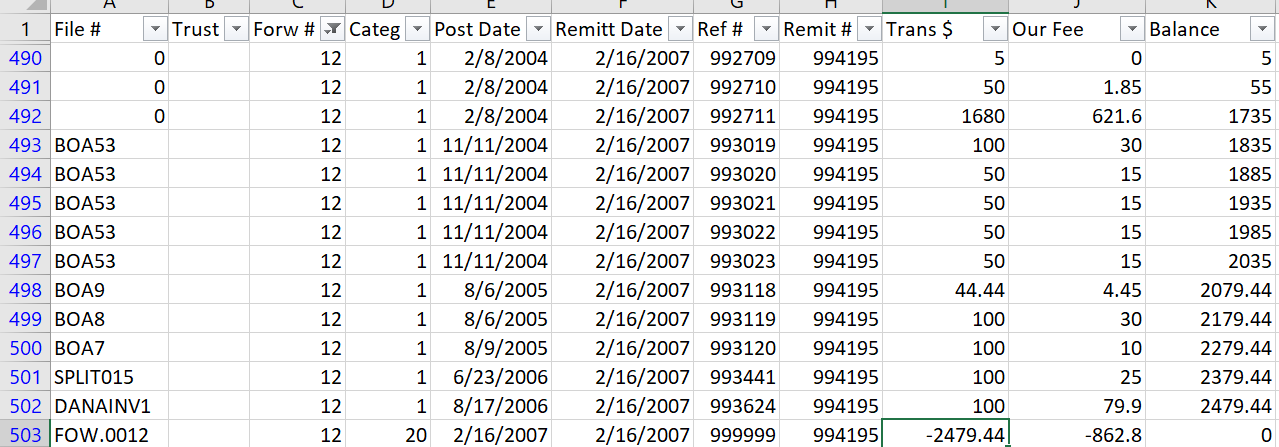
Export Running Balances (Forwbal) [2-2-9-8]
This report shows a running balance of every transaction by Forwarder. As you can see in the picture below, each transaction is listed, and the balance (by Client) is calculated. In addition, the actual remittance is listed showing (in this case) that the balance returned to $0.00 when remitted. It’s not always that tidy as you might hold payments until they clear, so the remittance can be less than the balance. The program creates a file in your “N:Folder” called FORWBAL.TXT. Load this file in Excel, and filter by the desired Forwarder, bank, or date ranges. In SQL-Sync, the table name is FORWBAL in the Open folder and needs to be added to the schedule, if desired.
Printing to PDF
Collection-Master supports printing to PDF both natively and using a Windows PDF print driver. The native PDF only works on 32-bit BRClient, so using the Windows PDF print driver is preferred.
Printing to “Windows Devices”
In addition to printing to actual printers, Windows supports output to various formats:
| Output | Notes |
| WIN:/OneNote | You will be prompted to select the Microsoft OneNote Database. |
| WIN:/PDF | You will be prompted to select the PDF document to be created (32 Bit BR Client Only). |
| WIN:/READER | The printer output will be displayed to your default PDF reader (32 Bit BR Client Only). |
| WIN:/OneNote | You will be prompted to select the Microsoft OneNote Database. |
| WIN:/XPS | You will be prompted to select the PDF document to be created. |
| WIN:/vMedia-BW or WIN:/ActMaskR | Print to vMedia. Note: printing to this port works, but is very slow! It took several minutes for vMedia to respond. |
| PRN:EXCEL_IT/EXCEL_IT | Output to Excel (/w Archive) |
| WIN:/Default | Prints to the default Windows printer. This can be helpful for selecting output devices that are “Difficult to configure in Collection-Master.” |
| WIN:/Select | Prompts the user to select the desired Windows printer. This can be helpful for selecting output devices that are “Difficult to configure in Collection-Master.” |
Notes:
- Set up Printers in 1-S-5 in Collection-Master.
- When defining a printer, use a “Partial Printer Name.” You cannot include spaces in the name.
SQL-Sync
If you are using SQL-Sync, create custom queries/reports. This is the DIY developer option, and you can create some very elaborate solutions.
Examples:
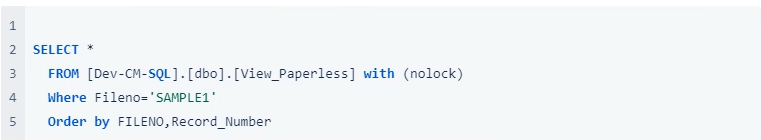
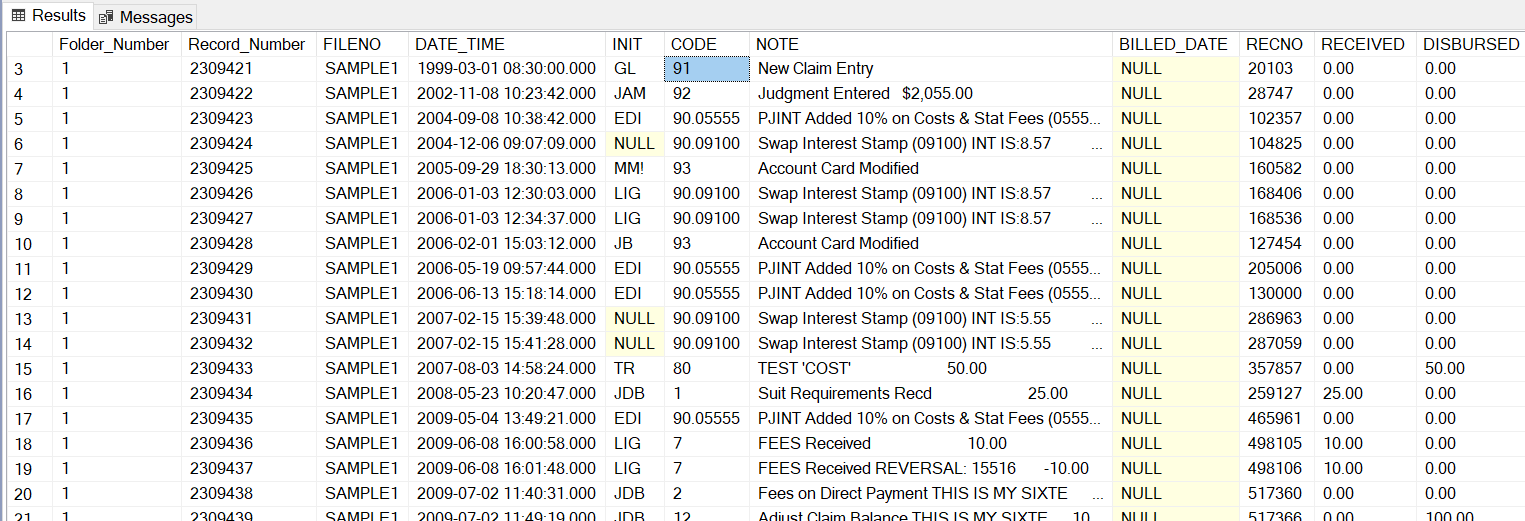
Paperless file notes
This sample is one claim, but you can include any filters that are appropriate.
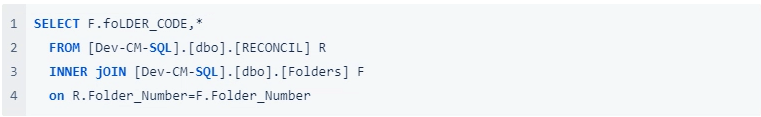
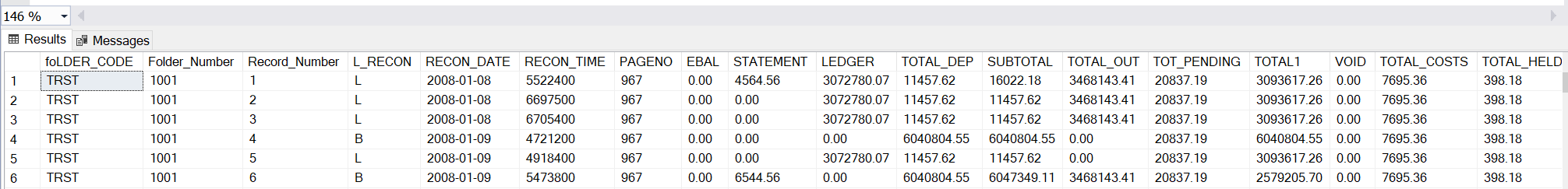
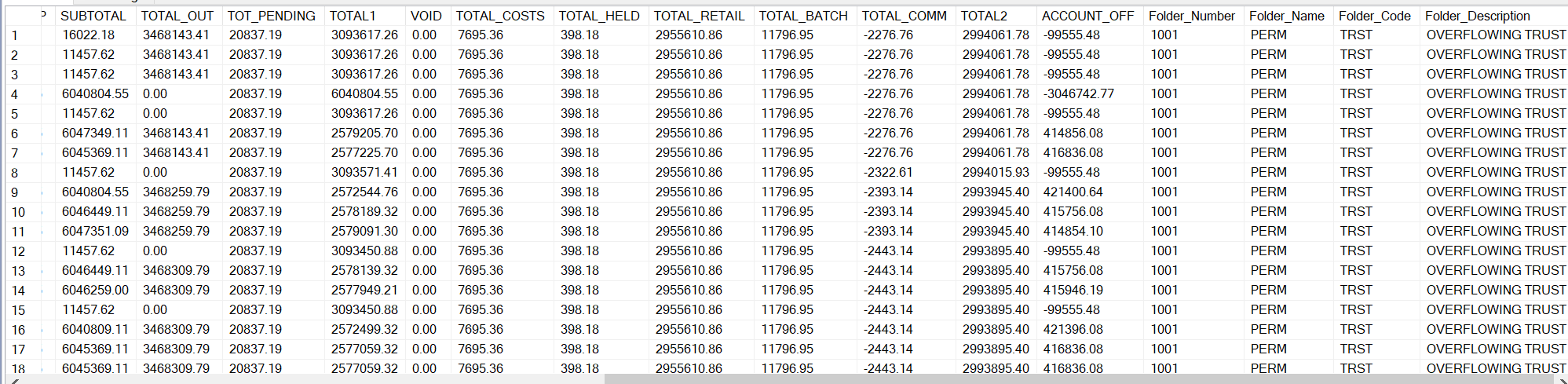
Reconciliation Balances
While you may be storing historical copies of reconciliation balances, the data is available in the “RECONCIL” table.