How to Secure Data in Collection-Master
Secure Data Configuration Instructions
Goal
The goal of this document is to better understand how to secure your data in Collection-Master. This document focuses on best practices for securing your data.
Secure Data Introduction
The world is compliance-crazy and client requirements are changing faster than the price of Bitcoin. So, keeping your business-critical software up-to-date is essential, particularly Collection-Master. Yet to do this in Collection-Master, you only need to run the latest version to benefit from Vertican’s ongoing software enhancements.
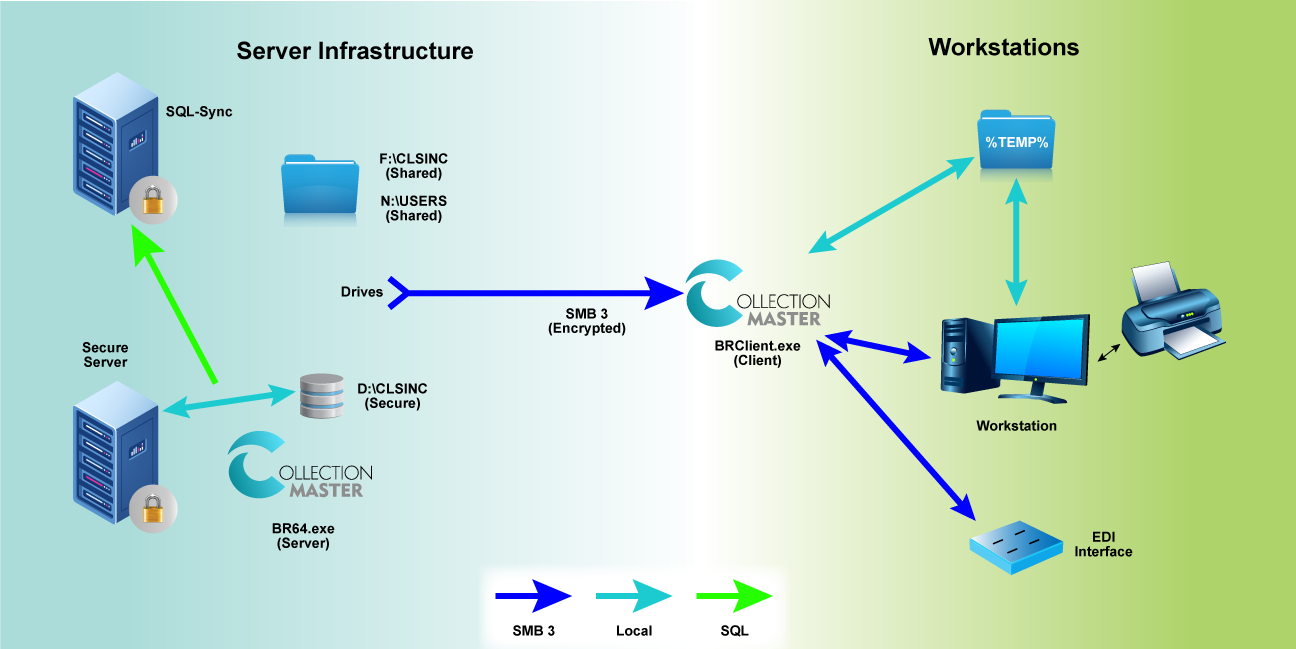
The introduction of Secure Data in Collection-Master has implemented significant features in compliance and security, allowing administrators to implement security protocols that restrict end-users from having direct access to sensitive data files. With the appropriate implementation and utilization of best practices, your office will:
- Enhance protection against crypto and other viruses by limiting direct access to critical data folders, thus significantly reducing the potential for infection.
- Mapless drives allow for greater security and compliance with critical data folders now available to be kept outside of F:\.
- Limit the data that can be moved/deleted (accidentally or maliciously) by users.
- Secure Data also allows for more targeted backups. This means:
- Backups of critical data folders are faster and more efficient.
- Can be performed more frequently to ensure more reliable and up-to-date data in the event of a restoration.
- Secure Data is not bogged down with potentially large directories such as OUTPUT.
- Implementing Secure Data requires use of the Client-Server.
- Due to the nature of Secure Data and the drives not being accessible to the end-user, ODBC will no longer function with its implementation.
Secure Data Configuration Instructions
Secure Data Introduction
Secure Data allows administrators to implement security protocols restricting end-users from being able to directly access sensitive data files.
As always, it is highly recommended that you have an accurate and reliable BACKUP prior to upgrading or changing your system. BE SURE it is a complete and verified backup. It is also suggested to first configure Secure Data in a test environment to ensure that any custom programming is compatible.
- Install Collection-Master 9.1 or higher.
- IMPORTANT: Before beginning to configure Secure Data ensure the following:
- All users are out of Collection-Master.
- Verify this through the Task Manager on the server that now processes such as BRServer.exe, br64.exe, etc. are running.
- Automated tasks, such as SQL_SYNC and Export2CM are temporarily disabled.
- QMonitor is not running.
- All users are out of Collection-Master.
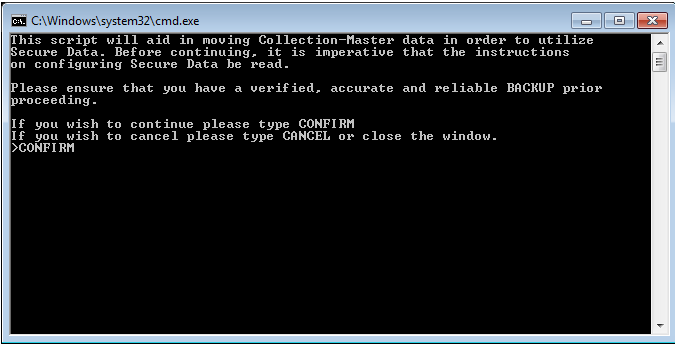
- On the server, run F:\CLSINC\BATCH\Move_2_Secure_Data.bat to move the COMMON/DATA/HISTORY/PERM & SHARE directories to the Secure Data location.
- Type CONFIRM to be able to proceed with the move to Secure Data.
-
- Note: Must be in ALL CAPS.
-
- Type CONFIRM to be able to proceed with the move to Secure Data.
-
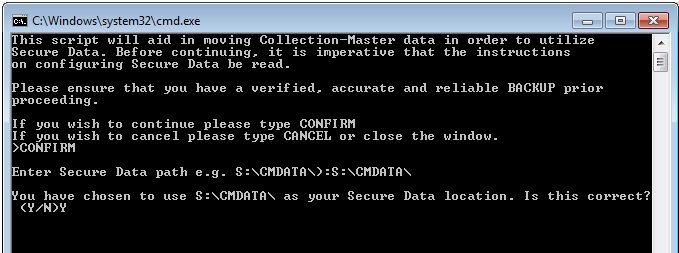
- Path of Collection-Master installation will automatically be designated.
- Path of Secure Data (e.g. S:\CMDATA\) must be specified by the user.
- Note: Mapped drive or UNC path can be provided.
![]()
-
- Confirm that the Secure Data location is accurate.
- Y – Begins the move to Secure Data5.
- N – Allows you to re-enter the Secure Data location.
- Note: Must be an uppercase letter.
- Confirm that the Secure Data location is accurate.
![]()
-
- Script will move the following directories using Robocopy:
- COMMON
- DATA
- HISTORY
- PERM*
- SHARE
- A log file documenting the move of the directories will be created and can be found in F:\CLSINC\Move_2_Secure.log.
- Script will move the following directories using Robocopy:
- MapDrive._CS must be manually configured to point to the location of the Secure Drive to be used. Below is a sample configuration assuming a Collection-Master installation of F:\CLSINC and a Secure Data path of S:\CMDATA\
- Rem [—- Start of CM-SETUP —-]
- Drive F,F:\,F:\,CLSINC
- Drive G,F:\,F:\,CLSINC
- Drive H,S:\CMDATA\,No_Drive,HISTORY
- Drive I,S:\CMDATA\,No_Drive,DATA
- Drive K,S:\CMDATA\,No_Drive,PERM
- Drive L,S:\CMDATA\,No_Drive,COMMON
- Drive M,S:\CMDATA\,No_Drive,SHARE
- Drive N,N:\,N:,USERS\[LOGIN_NAME$]
- Rem [—- End of CM-SETUP —-]
- Enter Collection-Master and validate trust accounts [2-S-3-F4] to auto-correct the change in the path name.
IMPORTANT: Implementing Secure Data requires the use of Client-Server. Ensure that any shortcuts defined are pointing to a Client-Server executable (BRClient.exe, BRClient64.exe, BRClient32.exe).
NOTE: Due to the nature of Secure Data and the drives not being accessible to the end-user, ODBC will no longer function with its implementation.
If you have any custom programming that is not currently compatible with Secure Data, contact our Client Success department to review the affected programs and determine the appropriate course of action.
Sample Move_2_Secure_Data process:
Encrypting Data at Rest
Modern storage devices support encryption at rest. Your storage device should be able to encrypt the data on the drives. While there are software solutions, they come at a significant performance expense. You should reach out to your IT professional and ask about encryption options on your storage devices. Encryption should be performed by your storage system to ensure reliability and performance.
Client-Server Encryption
When running Collection-Master in Client-Server mode, all communication with the storage device is direct to a local device on the server. In addition, the communication between the Server and Client is encrypted and protected by your Windows login. When combined with encryption at rest, it ensures that Collection-Master data and its communications are always encrypted.
Windows SMB3 – Encryption in Motion
Windows 10 and newer support the SMB3 protocol. You should reach out to your IT professional and ask them about encryption options for SMB3 file shares. Once properly configured, all communications between your workstation and the server will be over SMB3 and will be encrypted in motion. Combining encryption solutions with secure data will ensure that your system and your PII / NPI data are secure.
Other Applications
Collection-Master is usually not the only application on the network. As an example, you might export your data to Microsoft Excel or WordPerfect. The multi-layer encryption approach should also protect these applications If you are going to store data on your “C: Drive” you might want to use an encryption tool such as BitLocker or something provided by another vendor.
Network Architecture